Anonymity
The Bitcoin currency and associated transactions can, technologically, function in complete anonymity. However, the current production of the project is not quite as anonymous as it should be.
Contents
The main problem is that every transaction is publicly logged. Anyone can see the flow of Bitcoins from address to address (see first image). Alone, this information can’t identify anyone because the addresses are just random numbers. However, if any of the addresses in a transaction’s past or future can be tied to an actual identity, it might be possible to work from that point and guess who may own all of the other addresses. This identity information might come from network analysis, surveillance, or just Googling the address. The officially encouraged practice of using a new address for every transaction is designed to make this attack more difficult.
The second image shows a simple example. Someone runs both a money exchanger and a site meant to trap people. When Mr. Doe buys from the exchanger and uses those same coins to buy something from the trap site, the attacker can prove that these two transactions were made by the same person. The block chain would show:
- Import coins from address A. Send 100 to B. Authorized by (signature).
- Import coins from address B. Send 100 to C. Authorized by (signature).
Bitcoin transactions do not have a “from” address, but if the attacker believes that address B is controlled by Mr. Doe because the attacker received $5 from Mr. Doe’s PayPal account and then sent 100 BTC to that address then they can infer the identity of the party sending to C. This assumption is not always correct because address B may have been an address held on behalf of Mr. Doe by a third party and the transaction to C may have been unrelated.
Another example: someone is scammed and posts the address they were using on the Bitcoin forum. It is possible to see which address they sent coins to. When coins are sent which were previously send to this (the scammer’s) address, the addresses that receive them can also be easily found and posted on the forum. In this way, all of these coins are marked as “dirty”, potentially over an infinite number of future transactions. When some smart and honest person notices that his address is now listed, he can reveal who he received those coins from. The Bitcoin community can now ask some pointed questions, “Who did you receive these coins from? What did you create this address for?” Eventually the original scammer will be found. Clearly, this becomes more difficult the more addresses that exist between the “target” and the “identity point”.
You might be thinking that this attack is not feasible. But consider this case:
- You live in China and want to buy a “real” newspaper for Bitcoins.
- You join the Bitcoin forum and use your address as a signature. Since you are very helpful, you manage to get 30 BTC after a few months.
- Unfortunately, you choose poorly in who you buy the newspaper from: you’ve chosen a government agent! Maybe you are under the mistaken impression that Bitcoin is perfectly anonymous.
- The government agent looks at the block chain and Googles (or Baidus) every address in it. He finds your address in your signature on the Bitcoin forum. You’ve left enough personal information in your posts to be identified, so you are now scheduled to be “reeducated”.
You need to protect yourself from both forward attacks (getting something that identifies you using coins that you got with methods that must remain secret, like the scammer example) and reverse attacks (getting something that must remain secret using coins that identify you, like the newspaper example).
Staying Anonymous
By necessity the history of all the bitcoins must be highly public. However, if one has bitcoins on paid to address, one can theoretically choose the coins they spend in a way that will minimize the amount of information they leak. Choosing personally generated coins or an address that you know doesn’t reveal information would protect you. Unfortunately, the default Bitcoin client doesn’t support this currently, so you must assume that your entire balance can identify you if any of the addresses can.
You may consider a bitcoin to be “less-anonymous” when an attacker could feasibly find the true identity of a very recent owner of the bitcoin, perhaps because one of the bitcoin addresses was posted to a website, or because he knows some identifying information through other means.
If your balance has been contaminated by both anonymous and non-anonymous coins, you may take action to make it “clean”.
Recommended way of anonymizing your balance:
- Send however many coins you want to anonymize to a new eWallet account as a lump sum. There are other eWallet services however the more widely used the greater the potential for anonymity.
With this method an attacker will have to gain access to the eWallet service’s transaction logs to continue to follow you in the transaction history.
The protection that this method offers is significantly reduced if you are trying to anonymize more than about 10% of the total number of Bitcoins that the eWallet service holds. You’ll end up getting your own coins back instead of other users’ coins. Withdrawing Bitcoins more slowly and in smaller increments will help reduce this problem. Sending coins to an eWallet service in the largest single transfer possible will also help.
To further enhance your anonymity, you can:
- Send Bitcoins from one eWallet sevice to another and then to yourself. Each transfer needs to be painstakingly investigated and many transfers will present insurmountable difficulty.
Once you have an anonymous balance set up, be sure to keep your anonymous and non-anonymous balances completely separate.
A future version of the client will have more control which will allow the sender to specify which coins to use in a transaction[1].
In the future, trusted relay servers operating on the friendly addresses with enhanced privacy protocol could provide bitcoin users strong anonymity with increased convenience, thereby eliminating the need to make a trade-off between privacy and ease of use.
Helping other people stay anonymous
- Set up a real external mixing service. Make it like an eWallet service but make sure that a user never withdraws the same coins that are put in. Also delete empty addresses and transaction logs.
- Even if you’re not a programmer, you can make a slightly less secure version of an external mixing service (as a Tor hidden service, preferably):
- Set up two Bitcoin installations.
- Put some amount of BTC in installation B. This is the maximum amount of BTC you can deal with at once (for all customers).
- Customers send BTC to installation A. You send them an equal number of coins (or minus a fee) from installation B. Send as 10 to 50 BTC increments.
- Send all coins from A to B when all orders are satisfied. You can’t send coins from A to B if you have any orders that have not been satisfied from B.
- This can be automated, or you can do everything manually.
- Put lots of bitcoins in an eWallet service and keep it there. If anyone uses the anonymization method described in “staying anonymous” above, this will enhance it. Send in smaller increments if a large amount is transferred.
CoinJoin
While external mixers are useful and historically important, they have several problems. The mixer may also steal the customer’s coins. Thus the mixer service will depend significantly on it’s reputation to maintain customer’s privacy and not steal their money, which allows them to charge a significant fee far above the marginal cost which takes advantage of this reputation.
CoinJoin is a special kind of bitcoin transaction that solves these problems. It is a kind of smart contract which does not allow any party to steal the coins of any other party.
Legality
Obviously, using Bitcoin anonymity techniques for the purposes of money laundering is illegal, but participating or running schemes which others use for money laundering may also be illegal or at least leave the participant vulnerable to accusations of aiding criminals and terrorists. Bitcoin anonymity techniques involving bitcoins worth large amounts of money (over some value between FJ$1,100 and US$58,000, depending on your jurisdiction) is illegal in most jurisdictions, being in violation of anti-structuring laws.
Reasons for the lack of anonymity
- It is necessary to register each transaction publicly.
All users can see the cash flow of cryptocurrency as it passes from address to address. On one hand, users cannot identify this information as transaction numbers are random figures. On the other hand, if at least one transaction can be identified and its owner calculated it is probable that owners of other transactions will also be calculated. Information about owners can be obtained using network analysis from a surveillance tool or with the help of a search engine in order to find their address. Protection against identification and the increasing complexity of hackers’ attacks anticipate the need to attribute a new number to each new transaction.
- Transactions via exchangers can lead to the calculation of the Bitcoin account.
For example, if a certain Ivanov decides to use the services of exchangers, then do his shopping on the site intended to trap users, it is possible that another person who wants to calculate Ivanov’s address by sending two transactions will be able to prove that they have been generated by a single person from a single address.
- There is a danger that the address could be calculated by government commissioners.
For example, this information can be used to accuse a user of concealment of profits and tax evasion. The history of all transactions of the Bitcoin system must be public for security reasons. However, there are methods of minimising the amount of personal information being leaked on the network.
For example, mining using an address guaranteed to protect the user. Users must understand that such an absence of anonymity in the system is the basis for minimising the scope for “dirty” transactions, criminal activity and the Bitcoin system crashing. If the account contains anonymous and non-anonymous financial revenue, the user must make it “clean”.
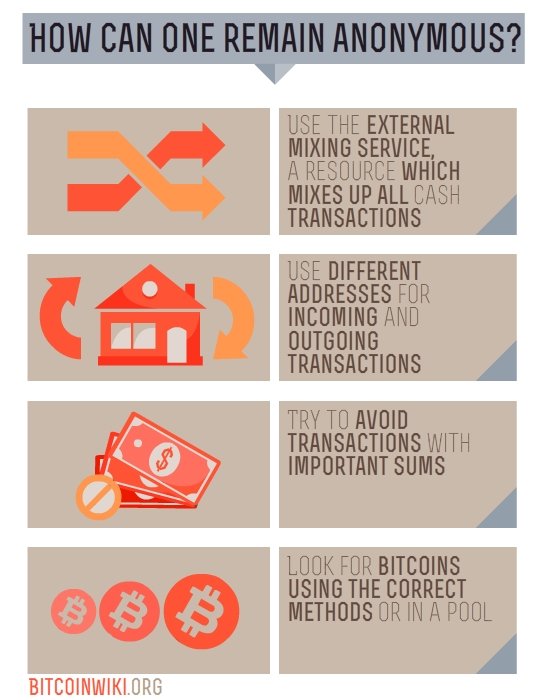
How can one remain anonymous?
There exist several classic methods of preserving anonymity:
- Use the services of an external mixing service, a resource which mixes up all cash transactions, then resends randomly money invested to different address with delays etc. The transaction sum is credited to the user account without commission. In theory, gathering of bitcoins in a large pool of transactions permits the transaction chain to be hidden.
- Use different addresses for incoming and outgoing transactions.
- Try to avoid transactions with important sums which can lead to a unique identification of the owner, as well as storing these sums in a single area.
- Look for bitcoins using the correct methods or in a pool, as in this case, they appear in a wallet of a mining expert.[2]
Legality of Anonymity
Anonymity is an unconditional right of a user to keep transactions secret. Nevertheless, anonymity which is a part of a system of money laundering or other criminal activities is illegal within the Bitcoin community.
Confidentiality vs. Anonymity
Confidentiality vs. anonymity – In the data collection process, when researchers are trying to obtain information from survey participants, they frequently indicate that the survey will be conducted anonymously or confidentially. There are distinct differences between the two terms and the researcher should be clear on the meaning of each, as they are very important for the protection of the participant. It is also important to remember that a study, with only one data collection method, cannot be both confidential and anonymous. Research participants should be informed beforehand of the type of data collection that will take place. They should also be informed of how long the data will be stored, where the data will be stored, and how it will be destroyed after an appropriate amount of time.
When data is collected and held anonymously, it indicates that there are no identifying values that can link the information to the participant; not even the researcher could identify a specific participant. Online survey tools are typically conducted anonymously, however, the researcher needs to be certain the IP address is not stored. The researcher also needs to keep in mind that too many identifying demographic variables could hinder the anonymity of the participants. In an anonymous study, the researcher needs to indicate how the participants will be kept anonymous. Be certain to include that no participants will be identified. It is also helpful to let the participant know that data will be analyzed at the group level.
When data is collected and held confidentially, the researcher can identify the subjects. One way of identifying the subjects is to assign an identifying number or code to each participant. Additionally, any survey that takes place in face to face environment is automatically labeled as confidential, as the researcher will know who provided the data. When data is collected confidentially, the information needs to be kept in a secure environment because the participants are identifiable. And similarly to anonymous data collection, it is also helpful to let the participant know that data will be analyzed at the group level in order to de-identify participants. Identifying numbers will not be presented in the results of the analyses. [3]
Links
- BitcoinFog — external mixing service.
See Also on BitcoinWiki
- Bitcoin address
- Security
- mixing service
- RFC: Bitcoin Mixnet
- Anonymity
- Patching The Bitcoin Client To Make It More Anonymous
- An Analysis of Anonymity in the Bitcoin System research by Fergal Reid, Martin Harrigan (discussion)
- Top Seven Ways Your Identity Can Be Linked to Your Bitcoin Address
- Tips to improve your bitcoin anonymity