Bitcoin weaknesses
Bitcoin has some security issues as it is potentially vulnerable to certain types of attacks: Sybil attack, 51% attack, DoS and others. In the article there is a review of the main disadvantages of Bitcoin cryptocurrency.
Contents
Bitcoin problems
Bitcoin like any other cryptocurrency has advantages and disadvantages. So, there is a downside of Bitcoin problems.
Wallet is poorly protected from attacks
By default Bitcoin wallet isn’t encrypted. For this reason, it becomes an easy prey to scams. However, the latest version of Bitcoin clients already contain codes for purse data protection, but the user must manually plug the cipher in.
A new wallet can be hacked through old password backups
Old copy of the purse with the old password can often be easily restored by creating a recovery program (for example, Apple Time-Machine): restoring an old purse with a password restores the current purse and your current password. Therefore, frequent password change do not guarantee complete security.
Solution to the problem: cryptocurrency creators must change the system so that a purse’s password change automatically creates a new wallet with a new password, and the accumulated savings should be automatically transferred to a new purse. With this if you try to restore a copy of the old wallet and your password you will fail. On the other hand, users who are not versed in the technical intricacies of creating purses, will not be able to recover the data of their savings and will lose their Bitcoins along with a purse.
Tracing transactions history
Tracing the history of transactions can be used to identify the address. It should be remembered that Bitcoin is not completely anonymous means of payment.
Sybil attack
Hacker can try to fill the network with nodes under his control, and other users will only be able to connect to blocks created specifically for fraud. How can this happen:
- The attacker blocks transactions from other users, disconnecting you from the public network.
- The attacker only connects you to the blocks he created in a separate network. As a result of this transactions will appear which will re-forward the money (Double-spending).
- The attacker can see all of your transactions through the use of special programs.
51% attack
In the early stages of its development Bitcoin just like any similar currency was vulnerable to the so-called “51% attack“: as long as attacker has more computing power then the rest of the network he can disconfirm others’ blocks confirming only their own, and thus receive 100% of all new Bitcoins and block any transaction at their discretion. (However they won’t be able to forward any transactions they want, because thay will not have others’ private keys to sign these transactions). Currently to conduct such attack in the Bitcoin network would require computing power many times more then the power of all TOP-500 rated supercomputers because the system became even better protected from these attacks after miners’ mass transfer from GPUs to ASICs.
Denial-of-Service attacks (DoS)
Sending a large number of “junk ” data to the node that handles transactions may hinder its work. Bitcoin has built-in protection against attacks such as “denial of service” but today this type of attack becomes harder with each new attempt.
For example the Bitcoin Satoshi 0.7.0 client blocks all suspicious nodes and transactions, does not allow transaction duplication, monitors DoS attacks emergence, catches intruders to the system, corrects errors, etc. In the latest eighth version of Bitcoin Satoshi client the ability to capture non-standard transactions (more than 100 kilobytes) and divide the distribution of information to memory and HDD were added.
Slowing time down
Hackers attack the network and slow down time within it making data transfer and messaging between users, updating the information in the network, the formation of blocks, chain and their confirmation by network members difficult.
Transactions vulnerability
Despite the fact that the Bitcoin transactions are signed with personal keys, this signature does not cover all the information that is processed to create a hash of the transaction. In fact there is an opportunity to change the transaction so that the hash changes, but the signature remains the same.
Based on this an attack can be organized that will withdraw funds from third-party services. The identifier in the original transaction is replaced, the money reaches the addressee, but they tell the technical support service that the original transaction has not arrived. As a result, the service can resend funds.
This feature is not considered Bitcoin protocol vulnerability, as it has been known since 2011, and can be eliminated by checking the original transaction.
Illegal data in blockchain
In some countries, the transfer of certain data is considered to be illegal. Such data can be carried in Bitcoin transactions and that in turn may lead to problems with law. In each node, there are rules prohibiting arbitrary (non-standard) data, but a small amount of fault data gets into network from time to time.
Security problems and bugs
Bugs can cause instability in the system protection. For example, information in the node should be updated in a short period of time. If due to a bug that did not happen, necessary information does not appear in the chain, incorrect data begins to spread through the network, etc. All this may cause interruption of the network for a few hours.
Modern versions of Bitcoin clients are created with the neccessity to react to bugs and correct mistakes in due time in mind.
Bitcoin problems in the future
Bitcoin hack
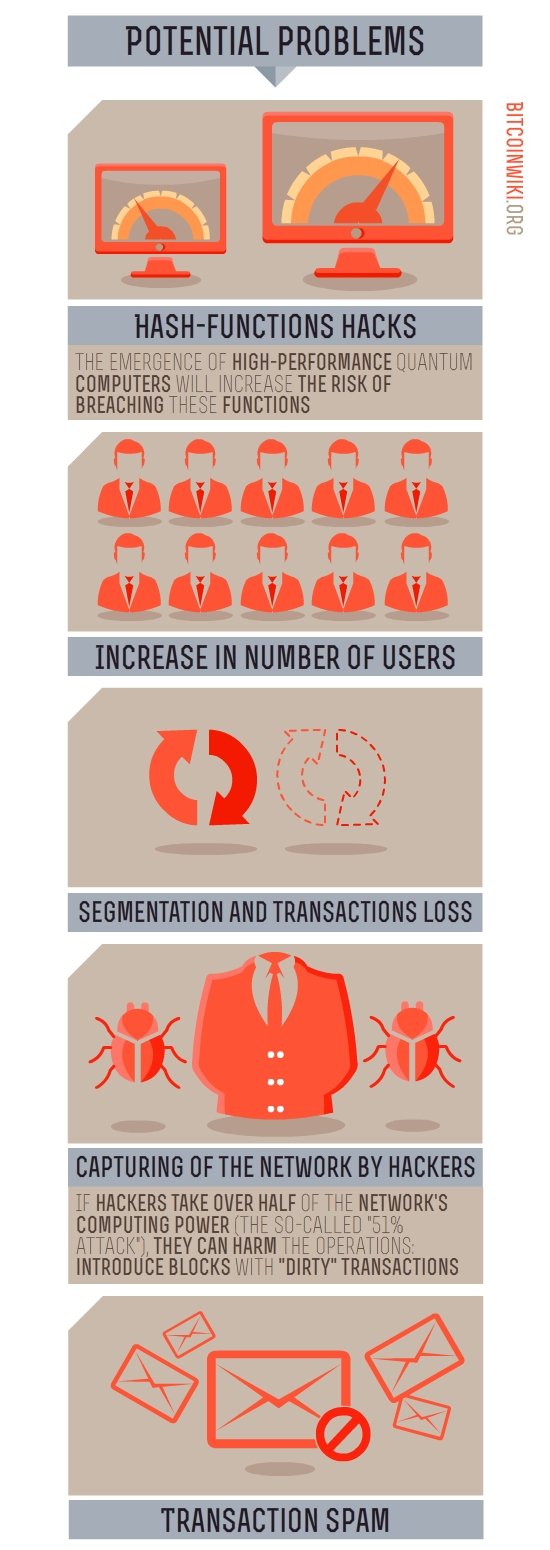
Hacks of hash functions: Algorithms to compute the hash functions of SHA-256 and ECDSA standards are considered impossible to hack with current computing powers. The emergence of high-performance quantum computers will increase the risk of breaching these functions. In this case the current hash function of Bitcoin can be replaced by more complex one.
Increase in number of users
Bitcoin network will cope with the influx of users. But if each user starts to use special software to hide their IP-addresses (which are available to other users by default), the network will not work.
Possible problems with segmentation and transactions loss
Difficulties with division of blocks and nods may arise, as well as confusion with the transactions and even loss of some. Bitcoin developers monitor the probability of such problems emergence as close as possible and upgrade the code in such way that will prevent difficulties in the network operation.
Capturing of the network by hackers
If hackers take over half of the network’s computing power (the so-called “51% attack”), they can harm the operations: introduce blocks with “dirty” transactions, conduct double-spending, separate the miners from the blocks, block transactions, etc. However, hackers will never be able to:
- Cancel the transaction
- Block transaction forwarding
- Change the number of coins issed for block’s closure
- Create coins from scratch
- Be engaged in sending coins, which they do not own
Transaction spam and “blank” transactions
Hackers can send false transactions, thus hampering the system operation. It is also possible to send out “blank” to produce network failures.
Not to be considered problems
Generation of excessive amount of addresses
The number of addresses doesn’t affect the network’s ability to operate. This can only take up space on the particular user’s HDD or their CPU resources.
Generation of blocks with lower complexity
An attacker could hypothetically create a chain of dummy blocks with reduced complexity. These blocks will be valid for the network, but their chain will not be able to connect with other chains in the network, since the rest of the nodes can verify that the blocks are fictitious (see Proof-of-work). Thus “deceptive” blocks will be rejected by the network.