Double Ratchet Algorithm
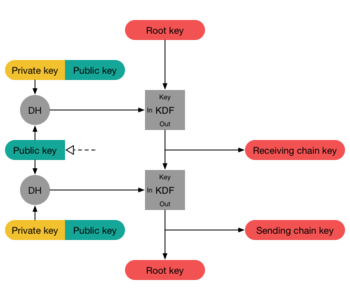
In cryptography, the Double Ratchet Algorithm (previously referred to as the Axolotl Ratchet) is a key management algorithm that was developed by Trevor Perrin and Moxie Marlinspike in 2013. It can be used as part of a cryptographic to provide end-to-end encryption for instant messaging. After an initial key exchange it manages the ongoing renewal and maintenance of short-lived session keys. It combines a cryptographic ratchet based on the Diffie–Hellman key exchange (DH) and a ratchet based on a key derivation function (KDF) like e.g. a hash function and is therefore called a double ratchet.
The developers refer to the algorithm as self-healing because it automatically disables an attacker from accessing the cleartext of later messages after having compromised a session key. The protocol provides confidentiality, integrity, authentication, participant consistency, destination validation, forward secrecy, backward secrecy (aka future secrecy), causality preservation, message unlinkability, message repudiation, participation repudiation, and asynchronicity.
Contents
Functioning
A client renews session key material in interaction with the remote peer using Diffie–Hellman ratchet whenever possible, otherwise independently by using a hash ratchet. Therefore, with every message a client using the double ratchet advances one of two hash ratchets (one for sending, one receiving) which get seeded with a common secret from a DH ratchet. At the same time it tries to use every opportunity to provide the remote peer with a new public DH value and advance the DH ratchet whenever a new DH value from the remote peer arrives. As soon as a new common secret is established, a new hash ratchet gets initialized.
As cryptographic primitives, the Double Ratchet Algorithm uses
- for the DH ratchet
- Elliptic curve Diffie–Hellman (ECDH) with Curve25519,
- for message authentication codes (MAC, authentication)
- Keyed-Hash Message Authentication Code (HMAC) based on SHA-256,
- for symmetric encryption
- the Advanced Encryption Standard (AES), partially in Cipher Block Chaining mode (CBC) with padding as per PKCS#5 and partially in Counter mode (CTR) without padding,
- for the hash ratchet
- HMAC.
Applications
The following is a list of applications that use the Double Ratchet Algorithm or a custom implementation of it:
- ChatSecure
- Conversations
- Cryptocat
- Facebook Messenger
- G Data Secure Chat
- Gajim
- Google Allo
- Pond
- Signal
- Wire
Other:
- In May 2016, Viber said that their encryption protocol is a custom implementation that “uses the same concepts” as the Signal Protocol.