Hidden Service

Hidden (Onion) services – servers configured to receive inbound connections through Tor network, which allow users to hide their locations while offering different kinds of services, such as web publishing or an instant messaging server.
Tor can also provide anonymity to websites and other servers. Servers configured to receive inbound connections only through Tor are called hidden services. Rather than revealing a server’s IP address (and thus its network location), a hidden service is accessed through its onion address. The Tor network understands these addresses and can route data to and from hidden services, even to those hosted behind firewall or network address translators (NAT), while preserving the anonymity of both parties.
Hidden services have been deployed on the Tor network since 2004. Other than the database that stores the hidden-service descriptors, Tor is decentralized by design; there is no direct readable list of all hidden services, although a number of hidden services catalog publicly known onion addresses.
Contents
How Tor Hidden Services Work
Instead of revealing a server’s IP address and its network location, a hidden service is not directly addressable from the global/public Internet and is accessed through its onion pseudo-URL. The first part of this domain name is a 16-character string (numbers and letters only) that is derived from the hidden service’s public key. These names appear randomly, and are necessary for the hidden server could respond to requests by authenticating themselves using their secret key to demonstrate they are the holder of the public key linked to that 16-byte service name. The Tor network understands these addresses and direct users to the anonymous service sitting behind that name. Unlike others, hidden services provide two-way anonymity. The server doesn’t know the client’s IP, like with any service, accessed over Tor, but the client also doesn’t know the IP of the server. This provides the ultimate in privacy cause it’s being protected on both sides.
Because hidden services do not use exit nodes, connection to a hidden service is encrypted end-to-end and not subject to eavesdropping. There are, however, security issues involving Tor hidden services. For example, services that are reachable through Tor hidden services and the public Internet, are susceptible to correlation attacks and thus not perfectly hidden. Other pitfalls include misconfigured services (e.g. identifying information included by default in web server error responses), uptime and downtime statistics, intersection attacks, and user error.
Description
TOR provides its users with the ability to hide their location, and at the same time offers them a variety of services, such as publishing or a web-based fast messaging server. Using “synchronization point” Tor, Tor, other users can connect to these hidden services, not being able to identifier the Steve features other users [1].
Technical details of the operation of the rendezvous Protocol
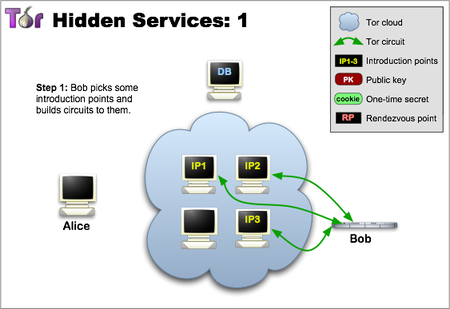
Before customers can connect to service stations, it must declare its support in the top network. Therefore, the service randomly selects some translators, creates chains to connect to them, and asks them to perform functions as points of introduction, informing them of your code to the public. Please note that in the following figures the green lines are the CEP connection, and not direct links. If you use a full tor circuit, it is difficult to associate an introduction point with the IP-Dress skirt server. Without Informing the Preface and other participants of the STO service data identification network (its public code), we do not want to disclose information about the location of thick skirt server (its IP address).
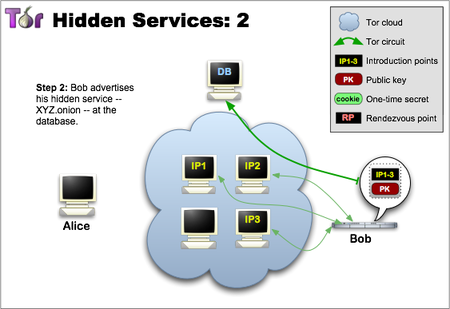
Step two: the Hidden service assembles a hidden service descriptor, containing its public key and a summary of each introduction point, and signs this descriptor with its private key. It uploads that descriptor to a distributed hash table. The description will be found by clients requesting XYZ.onion where XYZ is a sixteen-digit name that is unique and is generated using the public key of the service. After you complete this step, the hidden service is installed.
Although using an auto-generated service name may seem impractical, it serves an important purpose: Everyone, including the introduction points, the directory of the hash table being distributed, and of course the clients, can make sure they connect to the correct hidden service. See also the zooko hypothesis according to which from Decentralized, Secure and Significant you can achieve no more than two. Perhaps one day someone will use the name of a beloved dog as for hidden service names?
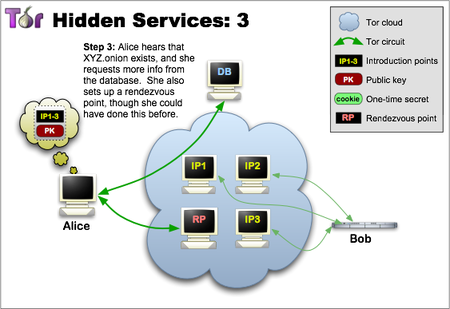
Step three: – the Client who wants to connect to the hidden service must first know its address. After that, the client can initiate connection establishment by downloading the descriptor from the distributed hash table. If there was a description for XYZ.onion (a hidden service may be offline or may have left the network a long time ago, perhaps you have also misspelled the onion address), then the client receives a set of introduction points and the correct public code. Around the same time, the client creates a connection chain to another randomly selected relay and asks it to act as a synchronization point, opening it a “one-time” secret.
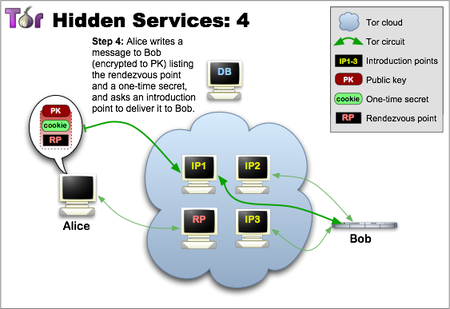
Step four: – when there is a description and the synchronization point is ready, the client provides an introductory message (encrypted in the public key of the hidden service) including the synchronization point address and the “one-time” secret. The client sends this message to one of the entry points, requesting it to be delivered to the hidden service. And again, the communication takes place through the Tor chain: no one can send a welcome message to the client’s IP address, and thus the client remains anonymous.
Step five: – the Hidden service decrypts the client’s message and finds the address of the synchronization point and a one-time key. The service creates a connection chain to the synchronization point and sends a one-time key there. At this point, it is very important that the hidden service adheres to the set of input protections required when creating new circuits. Otherwise, the intruder would be able to start his own relay and force the hidden service to create a random number of circuits in the hope that the false repeater would be perceived as an input node and thus, through time analysis, he learns the IP address of the hidden server. This attack was described by Slalom and syverson in their work “Location Hidden Servers”.
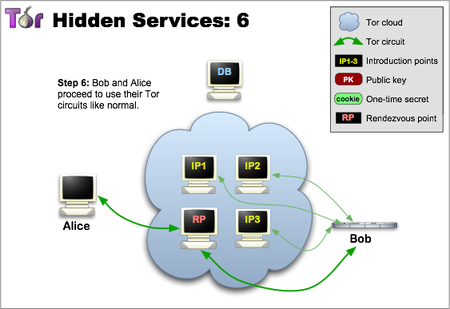
In a last step, the rendezvous point notifies the client about successful connection establishment. After that, both the client and the hidden service can use their synchronization point connection chain to communicate with each other. The meeting point simply retransmits (fully encrypted) the message from the client to the service and back[2]. One of the reasons why the introductory circuit is not used for the current communication is that no repeater should be responsible for the hidden service. That is why the rendezvous point never learns about the hidden service’s identity. In General, the full communication between the client and the hidden service consists of 6 repeaters: 3 of them were selected by the client, where the third was at the synchronization point, and the other 3 were selected by the hidden service.
Technologies used in Tor network
- TorStatusNet – http://lotjbov3gzzf23hc.onion/ is a microblogging service. It runs the StatusNet microblogging software, version 0.9.9, available under the GNU Affero General Public License.
- FlatPress is a blogging engine like -Wordpress blog http://flatpress.org/home/ – http://utup22qsb6ebeejs.onion/ –
- Snapp BBS works fine in OnionLand – http://4eiruntyxxbgfv7o.onion/ –
- PHP BBS – http://65bgvta7yos3sce5.onion/
- Nginx is a free, open-source, high-performance HTTP server and reverse proxy, as well as an IMAP/POP3 proxy server. – http://ay5kwknh6znfmcbb.onion/torbook/